Within the dynamic panorama of community safety, sustaining sturdy defenses towards evolving cyber threats is paramount. The firewall, serving as the primary line of protection towards unauthorized entry, performs an important function in safeguarding info methods. Common firewall audits are important to make sure the effectiveness and effectivity of those safety limitations.
This complete information explores what a firewall audit is, highlighting its significance, methodology, the benefits of using specialised firewall audit instruments, and a firewall audit guidelines with 7 finest practices.
What’s a firewall audit?
A firewall audit is a radical examination of firewall configurations, guidelines, and insurance policies to evaluate the safety posture of a company’s community. It entails scrutinizing the firewall rule base, evaluating the firewall’s bodily and digital features, and making certain compliance with inside insurance policies and trade requirements.
The significance of firewall audits
This part lists the explanation why performing a firewall audit is vital for your corporation.
1. Making certain community safety
A firewall audit performs a pivotal function in sustaining community safety. By figuring out and rectifying improperly configured guidelines, they assist shield delicate servers and key community gadgets from cyber threats.
2. Compliance and danger administration
Common audits are essential for making certain compliance with trade laws and inside safety insurance policies. They help in danger administration by figuring out dangerous firewall guidelines, redundant guidelines, and gaps within the safety posture.
3. Use instances in numerous environments
Firewall audits can be utilized within the following areas:
- Company environments: Common audits make sure that firewalls align with the company safety coverage and shield inside networks, together with the DMZ (Demilitarized Zone).1
- Public service suppliers: For web service suppliers and others, firewall audits assist handle direct site visitors and safeguard towards information breaches.
- Healthcare establishments: To safeguard affected person information and guarantee compliance with well being info privateness legal guidelines like HIPAA.2
- Monetary establishments: For securing monetary transactions and buyer information, and making certain compliance with the monetary trade laws.
Steps to performing a firewall audit
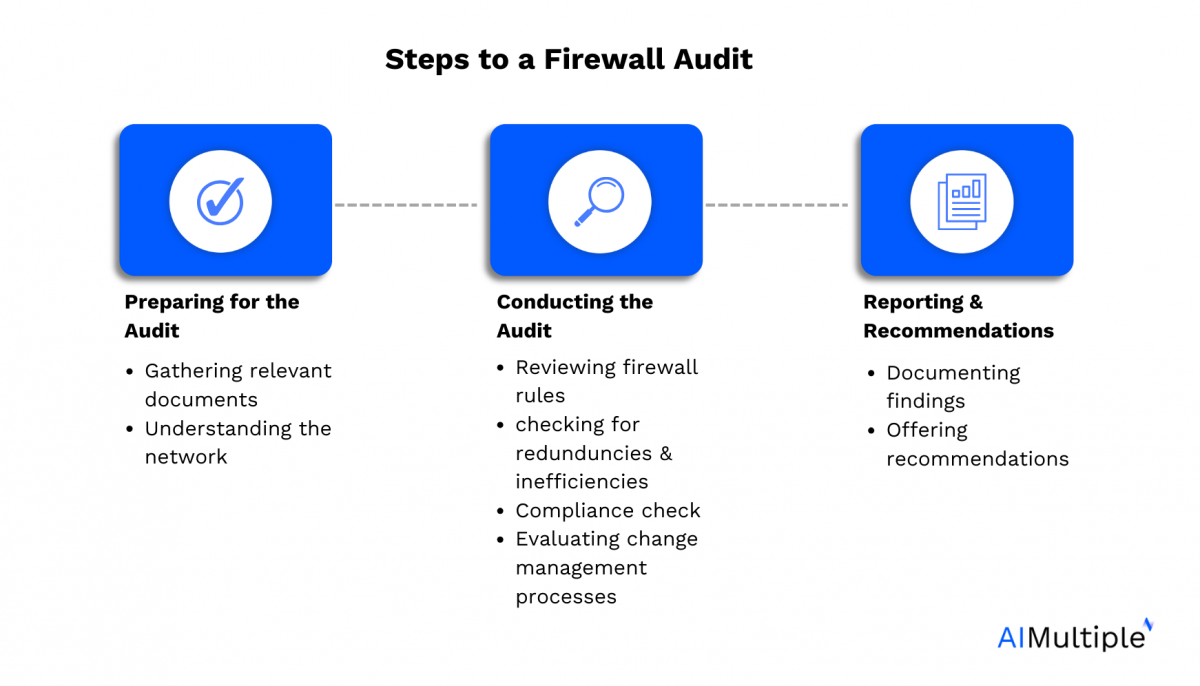
A firewall audit usually encompasses a number of key areas. You’ll be able to take into account the next steps or finest practices whereas conducting a firewall audit.
1. Making ready for the audit
1.1. Gathering related paperwork: Earlier audits, firewall logs, firewall configuration particulars, and related firewall vendor info needs to be reviewed.
1.2. Understanding the community: Achieve a complete understanding of the interior community, VPN parameters, firewall entry credentials, safety insurance policies, and another paperwork containing data on earlier firewall modifications.
2. Conducting the audit
2.1. Reviewing firewall guidelines: Assess every firewall rule for its necessity and safety. Take note of guidelines that permit dangerous companies inbound or outbound.
2.2. Checking for redundancies and inefficiencies: Determine and take away overly permissive guidelines, redundant guidelines, unused connections, and different vulnerabilities.
2.3. Compliance verify: Making certain alignment with company safety coverage, trade laws like PCI DSS, and information safety legal guidelines.
2.4. Evaluating the change administration course of: Guarantee a dependable change administration course of is in place for firewall modifications.
3. Reporting and suggestions
3.1. Documenting findings: Put together an in depth report outlining the findings, together with dangerous companies, improperly configured guidelines, and compliance points.
3.2. Providing suggestions: Counsel enhancements, corresponding to refining the rule base or enhancing working system safety.
Firewall audits might be carried out manually, however this course of is complicated and time-consuming, involving an in depth evaluate of firewall guidelines and configurations. As a result of danger of human error and the challenges in managing giant networks, many organizations desire utilizing automated instruments for effectivity and accuracy.
1. Enhanced accuracy and effectivity
Automated instruments cut back error-prone guide duties, growing the accuracy and effectivity of the audit course of since they will course of giant volumes of information a lot sooner than guide strategies.
2. Steady compliance and danger evaluation
Firewall audit software program allows steady compliance monitoring and real-time danger evaluation. Actual-time danger evaluation permits for quick identification and mitigation of potential safety threats. By analyzing information as it’s processed, these instruments present up-to-date assessments of the community’s vulnerability to new and rising threats.
3. Streamlining machine administration
This consists of duties like updating guidelines and configurations, which might be time-consuming and susceptible to error if completed manually. Automated instruments help in machine administration procedures, simplifying the firewall change course of, and making certain that firewall configurations are updated.
4. Optimizing firewall efficiency
Audit instruments assist determine dangerous guidelines, unused guidelines, and overly permissive guidelines, thereby optimizing firewall efficiency and strengthening the community’s safety posture.
Suggestions for incorporating firewall audits into organizational safety
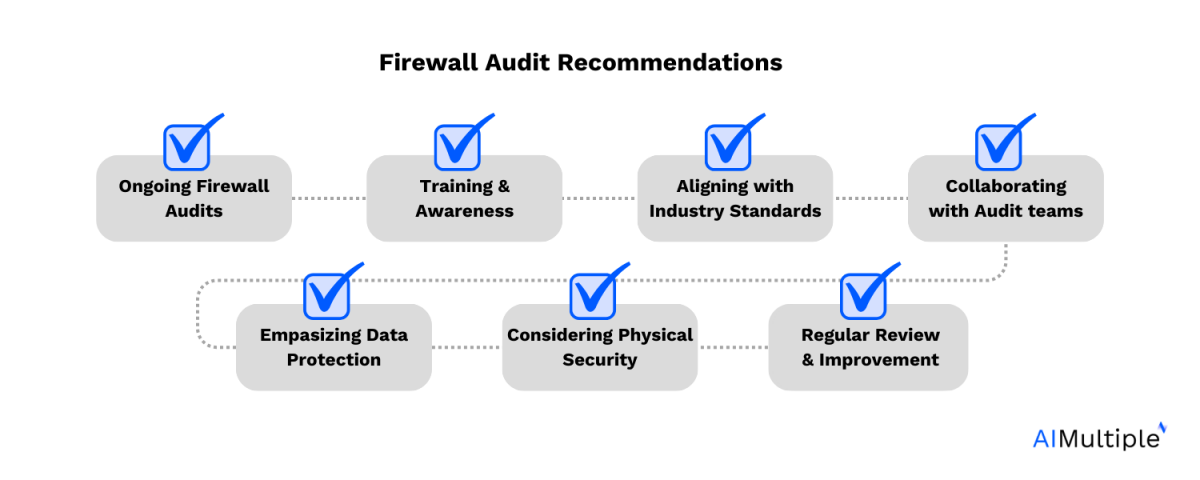
This part presents a firewall audit guidelines with 7 finest practices or suggestions on learn how to incorporate an efficient firewall audit system in your group.
1. Ongoing firewall audits
Common, ongoing audits are essential for sustaining a sturdy safety posture. They assist in figuring out modifications in inside community patterns, rising threats, and evolving compliance necessities.
2. Coaching and consciousness
Educating firewall directors and related workers in regards to the significance of firewall audits is crucial. It ensures that firewall change requests are correctly permitted and documented. You also needs to educate the workers of various departments to scale back the variety of dangerous companies outbound (Inner site visitors directed in the direction of exterior, probably harmful or untrusted web companies).
3. Aligning with trade requirements
Conducting firewall audits in accordance with these benchmarks and finest practices is essential not just for enhancing safety measures but in addition for making certain adherence to regulatory compliance necessities. This method helps keep a sturdy and safe community infrastructure.
4. Collaborating with audit groups
When the audit crew arrives, it’s vital for them to work intently with inside groups to realize entry to obligatory info and guarantee a complete audit.
5. Emphasizing information safety
Firewall audits are an important part of information safety methods. They assist safeguard delicate info from unauthorized customers and potential information breaches.
6. Contemplating bodily safety
Alongside digital safety measures, the bodily safety of firewall server rooms and administration servers is an integral a part of the general firewall audit course of.
7. Common evaluate and enchancment
The firewall audit course of needs to be an ongoing effort, with common opinions and updates to adapt to altering community environments and rising cyber threats.
In conclusion, a firewall audit is a essential part of community safety, offering a complete examination of the firewall configuration, the firewall rule base, and insurance policies. They make sure that firewalls are correctly configured to safeguard towards unauthorized entry, mitigate potential vulnerabilities, and keep optimum efficiency.
Additional studying
When you need assistance discovering a vendor or have any questions, be at liberty to contact us:
Discover the Proper Distributors
Exterior assets
- Demilitarized Zone. Wikipedia. Accessed: 19/December/2023.
- HIPAA. Wikipedia. Accessed: 19/December/2023.