As extra units develop into obtainable and organizations use extra information, it’s essential to shield this information. Using USB drives and different moveable storage units can result in information leaks. Machine management software program and practices are essential for managing this threat. These embody practices that assist management entry to information, like blocking or read-only permissions, to cease unauthorized information transfers and forestall information theft. This text is a information on the right way to use system management successfully, protecting finest practices, challenges, and options.
What’s system management?
Machine management is a software program utility that gives safety to your community. The appliance guards towards information loss attributable to information theft and malware adopted by unauthorized use of detachable units. The most well-liked exterior units are USBs, printers, smartphones, USB modems, cameras, detachable media, and extra units related by Bluetooth.
How does system management work?
Machine management options monitor and course of variables resembling community elements, log info, establish anomalies, and alter working programs as wanted, regardless of specs differing relying on the {hardware} wants and system provider. Machine management permits you to management and monitor exterior system conduct in accordance with predetermined authorization necessities.
Why do we’d like system management?
This part explains the significance of getting an efficient system management setting to safeguard delicate information. Efficient monitoring and controlling of person log experiences prevents organizations from lack of fame, authorized points, and, finally unhealthy funds.
1. Insider threats
Detachable units bear the burden of placing weak information in danger by spreading viruses and resulting in information loss. Established connections through Bluetooth or an enter port pose excessive dangers. Again in 2008, the U.S. Division of Protection suffered extremely from an information breach attributable to the insertion of an HDD in its community, which led to the leakage of confidential info within the Center East. The Pentagon had taken sturdy safety measures to forestall any recurrence. Safety measures have been shaped by such irrevocable accidents.
2. Insurance policies
Managing your group in compliance with rules issued by revered businesses such because the Worldwide Group for Standardization (ISO) not solely enforces safety requirements but in addition provides worth to your group by acknowledgment and encourages others to take action. On Forbes, you could find out extra about staying updated with information privateness requirements.1
3. Prices
Machine management is an efficient option to cut back the dangers to your funds. In response to the report ready by IBM in 2023, “the three most impactful value mitigators out of 27” had been every in contrast between its low- and high-level variations and with one another by the price of information theft. The next desk reveals the very best distinction between organizations with a excessive degree of DevSecOps and people with a low DevSecOps method.
Determine 1. Price of knowledge breaches
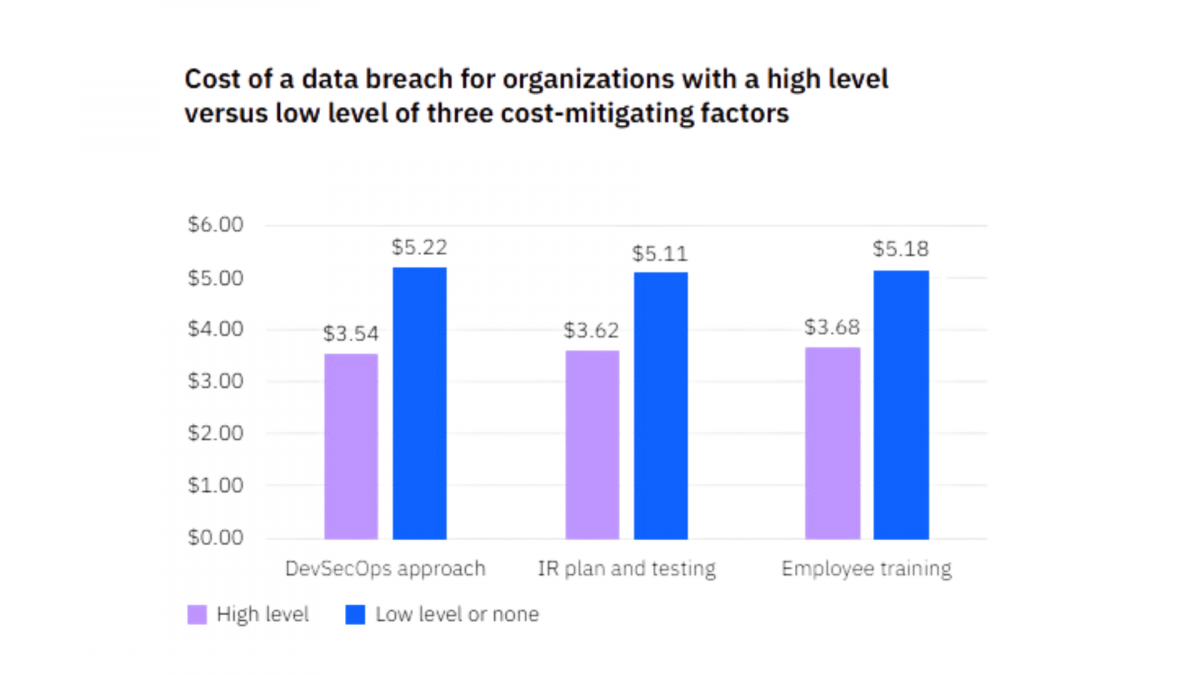
Supply: IBM2
Machine management challenges and options
Machine management software program is incessantly used to forestall information leakages attributable to detachable units. Machine management instruments display screen entry parameters, and block person entry or lock information when unauthorized system entry takes place.
1- Machine variety: Introducing new units right into a community requires a neat evaluation of units’ info concerning their operation system, authorization degree, and their varieties. All these elements might require totally different units of insurance policies and configurations, which may be difficult.
Answer: Choosing system management software program that may function in several programs with unreduced efficacy can rule out complicated operations.
2- Convey your individual system (BYOD): After the Covid-19 pandemic, individuals are inspired to work remotely or in a hybrid mannequin. Extra so, on-site working organizations allow their staff to work with their very own units. Although this method might save organizations prices, it additionally places them in danger by the unregistered broadening of its community. Asking its staff to have entry limits on their private units might injury the employer-employee relationship. The doorway of such detachable units, together with sensible telephones, might open a safety gap arduous to patch.
Answer: Educating staff about information safety and its administration will encourage the implementation of safety rules. With out disrespecting worker privateness and house, two events can transparently adjust to clear and intelligible described insurance policies.
3- Fixed updates and patches: Updating safety settings and putting in new instruments may be time consuming. Throughout patching and updates, to make sure whole safety, organizations are suggested by service suppliers to keep away from persevering with to function on units at hand.
Answer: Many system management software program include SaaS, cloud service, and digital equipment choices, which mitigate response time in accordance with the deployment form. These choices assist cut back response time primarily based on the kind of setup used. Additionally they cut back the necessity for handbook work when there’s a mismatch within the companies chosen by a company, making certain higher effectivity.
Machine management finest practices
Listed here are some finest practices that may allow enterprise leaders to implement system management of their group.
1- Usually replace firmware and software program
Builders enhance system management software program continuously. Guarantee that you’re utilizing the latest variations of system functions and software program. If there isn’t an automatic replace service obtainable, you might need to decide on handbook updating. Additionally, it’s important that service suppliers obtain suggestions concerning updates so as to facilitate amendments. Purposes which are not in use must be disabled and eliminated as a result of they could fail to match with updated safety necessities.
2- Authenticate and restrict authorization
This observe is likely one of the most essential to realize efficient system management. Think about using sturdy passwords and updating them often. You may as well leverage multi-factor authentication (MFA). Make it a observe to run authentication and authorization steps for every system. You may as well take into account storing log experiences and analyzing them to realize helpful insights into system efficiency and safety vulnerabilities.
3- Increase consciousness of your group
Know-how is all the time enhancing, so we have to work arduous to create phrases that target sustainability, respect, and defending rights. Whereas many insurance policies, like these from NGOs, are advisable however not required, some guidelines, just like the EU’s GDPR, should be adopted. Keep according to these insurance policies and maintain your group knowledgeable about them by coaching and educating them.
Additional Studying
Please check out the hyperlinks under to see extra details about information safety and information monitoring:
Should you need assistance discovering a vendor or have any questions, be happy to contact us:
Discover the Proper Distributors
Exterior sources
- 12 Tech Specialists’ Ideas To Assist Corporations Hold Up With Information Privateness Laws. Forbes. Accessed: 25/January/2024.
- Price of a Information Breach Report 2023. IBM. Accessed: 25/January/2024.